Network Protocol:
TCP/IP
Chong Ho (Alex) Yu, Ph.D., MCSE, CNE, CCNA |
What is protocol?
Networks need a set of rules and procedures to govern the
transmission of data. These rules together form a protocol. A
typical protocol includes the following specification:
- the type of error checking to be used
- data compression method, if any
- how the sending device will indicate that it has finished
sending a message
- how the receiving device will indicate that it has received
a message
Different network products have different protocols such as
AppleTalk in Macintosh networks, DLC protocol in HP network
printers, NetBEUI in Windows networks, IPX in Novell Netware
networks, TCP/IP in UNIX and the Internet. Nonetheless, TCP/IP is
gaining more and more popularity and therefore only TCP/IP will be
introduced here.
|
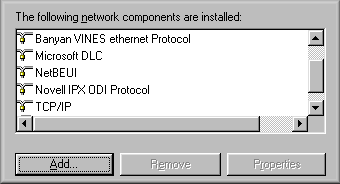
|
Different protcols are still
available but usually TCP/IP alone is sufficient for
networking. You should install what is/are needed rather
than accepting the default. More installed protocols will
slow down the performance of your computer, and even the
network.
|
TCP/IP was developed in the 1970s by and for the United States
Department of Defense (DoD) as well as several research
organizations. TCP/IP is not just a protocol. Rather it is a
protocol suite, which consists of Transmission Control Protocol,
User Datagram Protocol (UDP), and Internet Protocol. Only TCP and
IP will be discussed here. TCP divides data into smaller segments
for transmission as well as provides error checking and flow
control. IP performs the function of addressing and selecting the
routes of connection.
The following are the Open System Interconnection (OSI) model
and the DoD's TCP/IP model, which are conceptual frameworks of how
networks function. If you are not a network administrator, the
detail of these models are irrelevant to you. The most important
points are:
- TCP and IP operate at different layers of network
models.
- Data are formatted differently when they are passed from
one network layer to another.
- Computers communicate with each other by via ports using
TCP and IP addresses.
|
OSI
model
|
DoD (TCP/IP)
Model
|
Protocol
|
Data
format
|
|
Application
|
Application/Process
|
|
|
|
Presentation
|
|
|
|
Session
|
|
|
|
Tranport
|
Host to
Host
|
TCP/UDP
|
Segment
|
|
Network
|
Internet
|
IP
|
Packet
|
|
Datalink
|
Network access
|
|
|
|
Physical
|
|
|
IP Address
When you mail a letter in the post office, you need to
write down the address on the envelope. By the same token,
transferring data among computing devices requires addressing. IP
handles addressing by assigning an IP number to every computing
device on the TCP/IP network. I say computing device rather than
computer because a printer could have an IP address if TCP/IP
printing is used.
Let's use mailing address as an analogy again. A mailing
address consists of different levels such as country, state, city,
street, and apartment number. Similarly, an IP address is composed
of four chunks of 8-bit binary numbers such as 129.219.199.15,
which represent different levels of the address. For easier
identification, these binary numbers are translated into decimal
numbers that we use everyday.
The metaphor of physical address falls apart when it involves
the concept of logical addressing. In physical addressing,
apartment 1 and apartment 2 should be physically next to each
other. However, IP addressing groups computing devices logically
according to administrative needs. Two computers which carry IP
addresses as 120.219.199.10 and 129.219.199.11 may have no
geographical proximity at all.
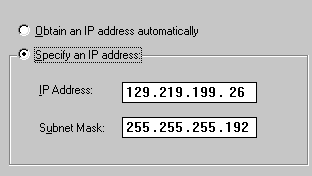
Subnet Mask
A state is divided into several counties. Similarly, a
network is spilt into many sub-networks. The Subnet Mask indicates
how many subnetworks are located in this network and determine
whether routing is necessary.
Router/Gateway
|
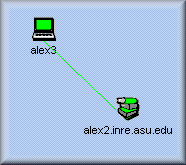
|
When computing devices are located in the same subnet,
they can connect to each other directly without an
intermediate station.
|
But when they do not belong to the same subnet, a router or a
gateway is needed to connect them.
In Mac networking the term "router" is used while in
Windows networking the term "gateway" is used. Today these two
terms are almost inter-changeable, but indeed they are slightly
different. A router passes information among networks with the
same protocol whereas a gateway connects different networks and
translates between protocols. *
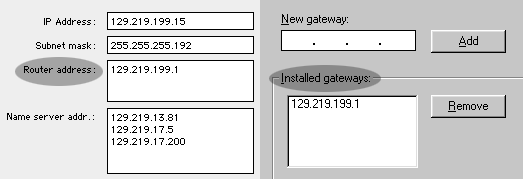
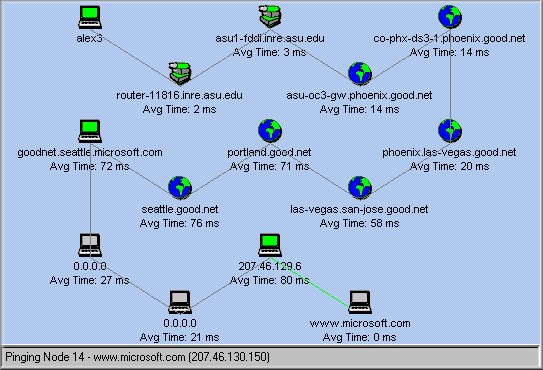
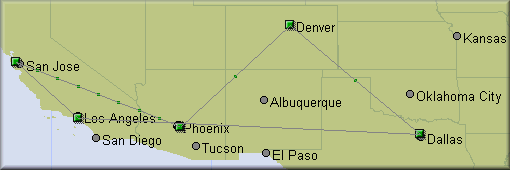
It is note-worthy that the principle of routing, to
certain extent, goes against common sense. For instance, if my
computer is located in Phoenix, Arizona and I want to access a Web
server in Tempe, which is less than 10 miles away from Phoenix, my
common sense will tell me that the best route is to go straight
from Phoneix to Tempe. Actually, routers may take several criteria
other than distance into account while determining the best route
(e.g. load, reliability...etc). The best route, as shown in the
following figure, may be Phoenix--Denver--Dallas--Los Angeles--San
Jose--Tempe.
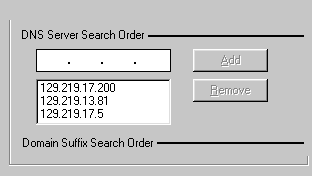
Domain Name Services
In order to pass information to the correct destination,
a router or a gateway must be able to identify the addresses of
computing devices. To achieve this, it looks up the address book
in a Domain Name Services (DNS) Server. A DNS server carries a
global database listing names and IP numbers of every TCP/IP
computing device. Usually in addition to the IP number, some
computing devices also has a domain name. For example, let's say
the IP address of a server is 129.218.11.111 and the name is
"www.alexyu.com" When you enter the domain name in a browser, DNS
translates the name into IP number so that a router knows which
computer is the destination.
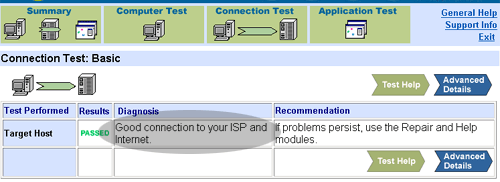
This look up procedure slows down the network traffic
slightly. It is faster to skip DNS and address a computer with the
IP number. Further, if the DNS server is down, you will not be
able to perform networking by using names. In this case, you
should use IP numbers instead. Actually it happens occasionally.
When the DNS servers are not reachable, the user could not do
anything with the Internet as usual even though everything else is
working properly. Unfortunately, when you use some tool to test
the network connection, it may show that no problem is found. The
following screen shot shows a typical example. The test result
returned by the software application shows that "good connection
to your ISP and Internet," but indeed DNS is down.
If an IP number alone is sufficient and even more efficient,
then why do people use domain names? Because it is easier to
remember "alexyu.com" than recalling "129.218.11.111." However,
one cannot just make up a domain name. Like IP numbers, domain
names must be unique and require registration. The mapping between
the two is stored in global databases. To register a domain name,
visit an authorized registration site such as networksolutions.org
or register.com
Dynamic DNS
It is important to note that unlike WINS, which will be
introduced in the following section, most DNS servers are static
i.e. they do not update themselves when a new IP and hostname are
assigned to a node. Nevertheless, a new standard called Dynamic
DNS is on the horizon. As its name implies, dynamic DNS is able to
receive registration of new IPs and hostnames automatically.
Although Windows 2000 has a feature to register the machine to
dynamic DNS servers, it may not work when your centralized DNS
server is static. Leaving the registration on would create
unnecessary traffic while your computer keeps sending
registration to a static DNS server.
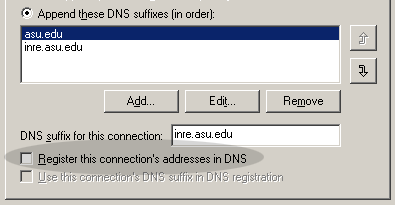
Windows Internet Naming Service
(WINS)
Like DNS, WINS also resolves names and IP addresses
except that the look up by WINS is specific for Windows computers.
DNS keeps track of all TCP/IP addresses on earth while WINS
usually keep records of Windows computer addresses in the LAN,
MAN, or WAN only. In addition, unlike DNS in which records are
static, WINS is dynamic i.e. A WINS server frequently scans
Windows computers currently available on the network for the
assigned IP addresses and automatically update these data.
Notes: Windows 2000 uses DNS to replace WINS. If you
have a pure Windows 2000 network, WINS is not neccessary.
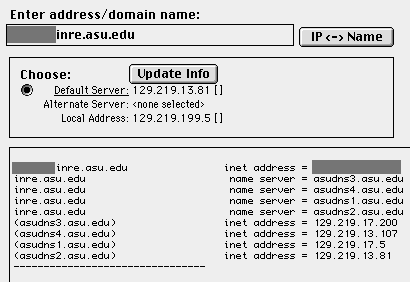
NS Lookup
You may wonder how you can get the above information (IP,
DNS, WINS...etc.). Ask your network administrator, of course. But
what if he is not around? A quicker way is to use a software
package for Name Services Lookup (NS Lookup), which is available
in both PC and Mac platforms. The following figure shows an
example of Mac NS Lookup. When you enter a hostname or a IP
address into the search field, NS LookUp can consult available DNS
servers and return the translated IP number or the hostname. When
you press the submit button, it can reveal more information such
as the IP numbers of the router, DNS servers, and WIN servers
associated with the computer. This tool is handy when you forgot
this information. For instance, once my coworker and I wiped out a
server's hard drive and did a clean installation. However, he
forgot to write down the IP numbers of the server, the router, the
DNS servers, and the WINS servers. He could remember only the
hostname of the server. As you expect, NS LookUp rescued us!
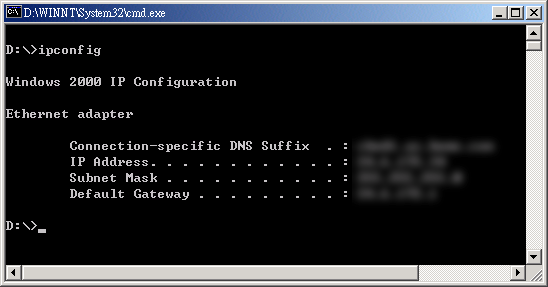
IPConfig
In addition to NSLookUp, another handy TCP/IP-related
tool is IPConfig (for Windows NT and Windows 2000). When you
cannot connect to the Internet, don't panic. First, open a
command-line session (a DOS-like window) by typing cmd in
Run. Then type IPCONFIG in the command session window. As the name
implies, IPConfig shows you the TCP/IP configuration of your
computer. From there you can see whether everything is configured
properly. To reveal more details, type IPCONFIG/ALL. If
your computer's OS is Windows 9x, please use WINIPCFG.
Socket/Port
The preceding section explains that TCP/IP is a protocol
suite, IP and subnet mask are parts of the addressing scheme, and
DNS and WINS are tools for address/name resolution. However, two
computers need more than a protocol suite and addresses to
establish a communication channel. They need a socket:
Socket = port + IP address + Transport layer
protocol
Ports in a computer are like "airports." They are points of
entry for data transportation. For example, a Web server opens
Port 80 for users to browse webpages; a FTP server opens Port 21
for users to upload and download files. Usually ports are
transparent to users. Nevertheless, you may want to know more
about it if you are curious about how a hacker intrude a computer
system. First, the hacker must know the IP address of the target
computer. Second, he/she uses port scanner software to look for
all vulnerable ports of a computer. When she/he finds an open port
and sends a compatible protocol, a socket is established and the
computer is hacked!
The first line of defense is NOT to expose your IP
address. If your computer is not a public server but you still
need to provide some network services to your coworkers, you can
change the port number from the default setting to something else.
For example, the default port number of a FTP server is 21. If you
change it to 9999, then your coworker must specify the exact port
number in order to access the server.
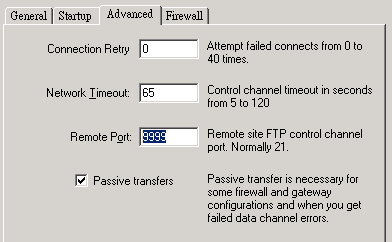
Another way to secure your computer is to disable unneccessary
services so that unused ports are shut down. Also, you can install
a Firewall to block malicious port scanning. A firewall is
a software- or hardware-based product that prevent unauthorized
users from gaining access to a computer network or that monitor
transfers of information to and from the network.
Note
* Do not perceive that a router is only for big networks
such as inter-networks across continents. You can have a router at
your home. A router, by definition, is a device to connect two
distinct networks. At home you can use a Cable modem/DSL router to
connect your local area network (LAN) inside your house with the
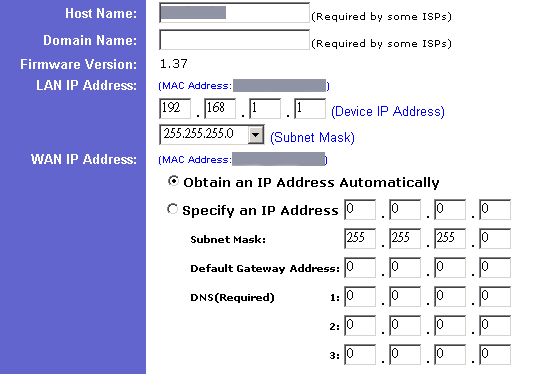
wide area network (the internet). The following figure shows the
configuration of a "home" router. As you see, the configuration
includes information of LAN IP and WAN IP. Basically, the WAN IP
is assigned by your internet service provider and the LAN IP is
assigned by the router.
In addition, a router is not necessarily a specialized
device. Any computer that has multiple network interface cards can
be configured to be a router. Both Novell Netware and Windows 2000
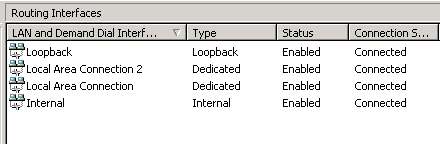
Server has built-in IP routing capability. The following figure is
a screen shot of the IP routing configuration in Windows Server.
Navigation


















